Libreria dei virus
L’analisi delle tecnologie utilizzate dai malfattori ci permette di trarre conclusioni su possibili vettori dello sviluppo del settore dei virus affinché possiamo affrontare le minacce future in modo ancora più efficace. Scoprite anche voi come funzionano in sistemi infetti determinati programmi malevoli e come affrontarli.
Android.Pincer nella libreria di virus:
Android.Pincer is a family of malicious software running on Android mobile devices. The main purpose of this malware is to intercept incoming text messages and forward them to the violator.
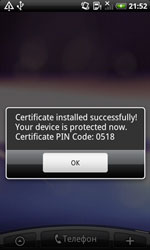
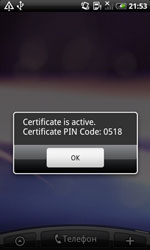
If started by careless users, the Android.Pincer Trojans display a message about supposedly successful installation of a security certificate to the mobile device.
These malicious programs can be loaded with the operating system bootup as a background service. For this, the malware registers an appropriate system service.
After loading, Android.Pincer Trojans are connecting to a remote server, which address can differ for each version of the malware (for example, http://89.144.xx.xxx/gate/gate.php, https://img-xxxxx.com/android_panel/gate.php), and uploading the following information about the mobile device to the server:
- device model;
- device serial number;
- IMEI number;
- telecom operator name;
- mobile phone number;
- default system language;
- operation system version;
- root-access availability details.
Then these malicious programs are waiting for further instructions via SMS control messages of the “command: [command name]" structure. Cybercriminals may provide one of the following directives:
- start_sms_forwarding [phone number] – start intercepting messages from the specified phone number;
- stop_sms_forwarding – stop intercepting messages;
- send_sms [phone number and text] – send an SMS with the specified parameters;
- simple_execute_ussd – perform a USSD-request;
- stop_program – stop working;
- show_message – display a message on the mobile device screen;
- set_urls – change address of the C&C server;
- ping – send an SMS with text “pong” to the phone number specified earlier;
- set_sms_number – change the phone number to which the “pong” text is sent.
Android.Pincer Trojans send contents of intercepted text messages to the C&C server while also providing subscriber’s name and phone number for each SMS.
Vulnerabilità per Android
Secondo le statistiche ogni quinto programma per SO Android contiene una vulnerabilità (ovvero un "buco"), il che permette ai malfattori di introdurre con successo trojan mobili sui dispositivi e di eseguire le azioni richieste.
Auditor di sicurezza in Dr.Web per Android farà la diagnostica e l’analisi della sicurezza del dispositivo mobile, proporrà soluzioni per risolvere i problemi e le vulnerabilità rilevate.