SHA1:
- 90dce3ff33ae46da6937d6ca7068dc64dbfebe76
- beb84b80429440adeb06d973ffc4acb99d6e344b
It is a Windows version of the Linux.Ekoms.1 Trojan. Once launched, the malicious program checks the %appdata% folder for the following files:
- "Skype/SkypeHelper.exe"
- "Dropbox/bin/DropboxHelper.exe"
- "Google/Chrome/nacl32.exe"
- "Google/Chrome/nacl64.exe"
- "Mozilla/Firefox/mozillacache.exe"
- "Adobe/Acrobat/AcroBroker.exe"
- "Hewlett-Packard/hpqcore.exe"
- "Hewlett-Packard/hpprint.exe"
- "Hewlett-Packard/hpscan.exe"
If the specified files are not found, the Trojan saves its own copy named as one of the mentioned files randomly chosen.
Apart from screenshot taking, Trojan.Ekoms.1 creates two file types: the one is appended with the .kkt extension and stores information on key strokes, and the other, with the .ddt extension, contains a list of files in folders. These two files are then transmitted to the server. It is noteworthy that the files are also mentioned in Linux.Ekoms.1, but it does not have a code responsible for their processing. Like its counterpart, Trojan.Ekoms.1 can record sound and save it in the WAV format. However, this function is not used in this modification as well.
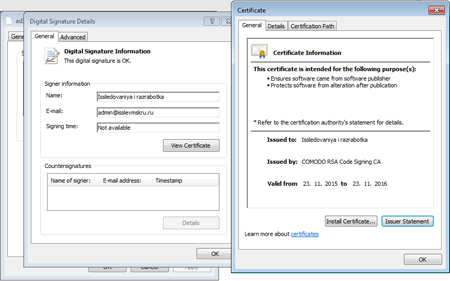
The Trojan has a valid digital signature registered to some company called “Issledovaniya i razrabotka”, and a root certificate is issued by Comodo.