Libreria dei virus
L’analisi delle tecnologie utilizzate dai malfattori ci permette di trarre conclusioni su possibili vettori dello sviluppo del settore dei virus affinché possiamo affrontare le minacce future in modo ancora più efficace. Scoprite anche voi come funzionano in sistemi infetti determinati programmi malevoli e come affrontarli.
UC Browser nella libreria di virus:
UC Browser for Android has been found to have a hidden ability to download and launch new software components, bypassing Google Play servers. This feature violates Google’s policy and poses a potential threat. If cybercriminals gain control of the browser's command and control server, they can use the built-in update feature to distribute any executable code, including malware. Besides, the browser can suffer from MITM (man-in-the-middle) attacks. The vulnerability has been found in UC Browser version 11.1.5.890 and later, as well as UC Browser Mini version 11.0.2 and later.
The further description of the potentially dangerous browser feature is based on its latest available version 12.10.8.1172, distributed via Google Play.
Browser structure
UC Browser has a complex modular architecture. It consists of several software components (plug-ins) with varying number and purpose, depending on the browser version. See below the list of currently available application modules.
Plug-ins in the form of .dex and .jar files:
- \assets\dexes\imagecodec_java.jar
- \assets\dexes\pictureviewer_java.jar
- \assets\moduleDexes\barcode.dex
- \assets\moduleDexes\ucmusic.dex
- \lib\armeabi-v7a\libcore_jar_kj_uc.so (a .jar module with a renamed extension)
- \lib\armeabi-v7a\libsdk_shell_jar_kj_uc.so (a .jar module with a renamed extension)
- \lib\armeabi-v7a\libsgmain.so (a .jar module with a renamed extension)
Plug-ins in the form of executable Linux libraries:
- /lib/armeabi-v7a/libBrowserShell_UC.so
- /lib/armeabi-v7a/libbtm.so
- /lib/armeabi-v7a/libchromaprint-jni.so
- /lib/armeabi-v7a/libcrashsdk.so
- /lib/armeabi-v7a/libdaemon_manager.so
- /lib/armeabi-v7a/libdalvikhack.so
- /lib/armeabi-v7a/libhelp.so
- /lib/armeabi-v7a/libhomodisabler.so
- /lib/armeabi-v7a/libicui18n_uc.so
- /lib/armeabi-v7a/libicuuc_uc.so
- /lib/armeabi-v7a/libimagecodec.so
- /lib/armeabi-v7a/libimagehelper.so
- /lib/armeabi-v7a/libjpeg_private.so
- /lib/armeabi-v7a/libLFGlJni.so
- /lib/armeabi-v7a/libmarsulog.so
- /lib/armeabi-v7a/libmissile.so
- /lib/armeabi-v7a/libpng_private.so
- /lib/armeabi-v7a/libresm.so
- /lib/armeabi-v7a/librism.so
- /lib/armeabi-v7a/libstlport_shared.so
- /lib/armeabi-v7a/libtnet-3.1.14.so
- /lib/armeabi-v7a/libuccrypto.so
- /lib/armeabi-v7a/libucinflator.so
- /lib/armeabi-v7a/libunet.so
- /lib/armeabi-v7a/libv8uc.so
- /lib/armeabi-v7a/libwebp_private.so
- /lib/armeabi-v7a/libwebviewuc.so
- /lib/armeabi-v7a/libzstd.so
- /lib/armeabi-v7a/libzxingjni.so
Some of these components load upon application launch, while others load when needed for a working browser.
Hidden update feature
The application contains the com.uc.aerie.updater package, which uses the Tinker library to install updates without reinstalling the program. The com.uc.deployment.UpgradeDeployService service is responsible for receiving updates.
When we were testing the application, an update request to the server http://puds.ucweb.com/upgrade/index.xhtml?dataver=pb was followed by downloading the native library libpicsel.so, located at:
http://gjxz2.ucweb.com/files/OfficeSo/en-us/352/OfficeSo_V1.0.0.0_android_pf145_(Build1704181610).zip?auth_key=1543835590-0-0-3643380ec3205b86d14d33a6f4cfc4cd&vh=fc244462e5aad8ac98fc1111a2512cfa&sf=2172301&SESSID=6ef76125863cf36e2410804ae2090430
This library is used by the com.picsel.tgv.lib package. It is not malicious and is designed to work with MS Office documents and PDF files. Initially, the browser did not contain the library. Thus, the program can expand its capabilities, downloading modules from the Internet.
After downloading, libpicsel.so was saved to the /files directory of the browser and launched in the com.uc.browser.office.sdk.c class:
if(this.tgv == null) {
Context context = ContextHolder.mContext;
StringBuilder sb = new StringBuilder();
sb.append(com.uc.browser.core.download.d.e.filesdir);
sb.append("libpicsel.so");
this.tgv = new TGVCore(context, sb.toString());
}
The com.picsel.tgv.lib.TGVCore class loads the library into memory and calls methods from it:
public TGVCore(Object context, String path) {
super();
this.initCore(context, true, path);
}
private void initCore(Object context, boolean absolute, String path) {
if(absolute) {
System.load(path);
}
else {
System.loadLibrary(path);
}
TGVCore.initStaticData();
this.initNative(context);
}
private native void initNative(Object arg1) {
}
private static native void initStaticData() {
}
Vulnerability to MITM attacks
Commands to download new plug-ins are sent encrypted from the command and control server. However, UC Browser communicates with a remote host via an unprotected HTTP channel. Thus, cybercriminals can perform MITM attacks.
See below an analysis of algorithm for communication between the browser and the command and control server, as well as downloading new modules.
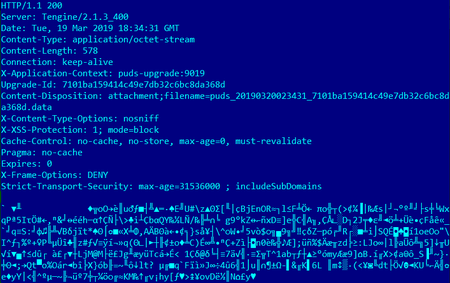
A server response example when the program is accessing http://puds.ucweb.com/upgrade/index.xhtml?dataver=pb:
The server response contains an encrypted command with the parameters, required to download the plug-ins. The command body is AES encrypted in the CBC (Cipher block Chaining) mode; the encryption algorithm is indicated with offset 2. The encryption key number is indicated with offset 0x10.
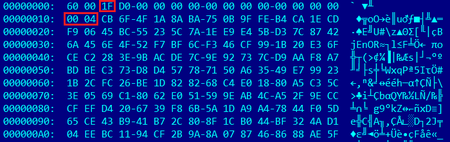
See the image below for an example of an encrypted command:
The command is decrypted using the libsgmainso-6.4.36.so native library (SHA1 — 8b998ab3cc6c9c4f877043b5113851035625c19b).
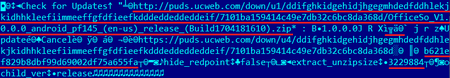
The decrypted command looks like this:
After decrypting, UC Browser downloads a ZIP archive with a new plug-in using the link, specified in the command, then checks the MD5 checksum and the LEB128 encoded archive size, as well as the file size in the archive. It does not verify the file’s digital signature.
Thus, to perform an MITM attack, cybercriminals will only need to hook the server response from http://puds.ucweb.com/upgrade/index.xhtml?dataver=pb, replace the link to the downloadable plug-in and the values of attributes to be verified, i.e. MD5 of the archive, its size, and the plug-in size. As a result, the browser will access a malicious server to download and launch a Trojan module.
Vulnerabilità per Android
Secondo le statistiche ogni quinto programma per SO Android contiene una vulnerabilità (ovvero un "buco"), il che permette ai malfattori di introdurre con successo trojan mobili sui dispositivi e di eseguire le azioni richieste.
Auditor di sicurezza in Dr.Web per Android farà la diagnostica e l’analisi della sicurezza del dispositivo mobile, proporrà soluzioni per risolvere i problemi e le vulnerabilità rilevate.