SHA1:
- bb5d4619ee47927c3f25257453c0ca1e8c1c364f
SHA1 packed:
- c6b662f117caf3496daf39a59c38458359f342b3
SHA1 unpacked:
- 144534e3c69b5082936d6096a13b2b966a5ef08c
One of the banking Trojan modifications for Android OS, known as Anubis. Distributed and disguised as innocuous applications. This malicious program is based on the source code of the Trojan Android.BankBot.149.origin.
Android.BankBot.325.origin can receive the following commands from the managing server:
- Send SMS – sending SMS messages containing a defined text to the number specified in the command;
- Start USSD – executing USSD-request;
- Start Application – launching the application specified in the command;
- Replace URL Admin Panel/Forwarding – changing the address of the managing server;
- Get all SMS – sending copies of SMS messages stored on the device to the managing server;
- Get all installed applications – receiving information about applications installed;
- Get all permissions – checking the availability of the additional permissions for functioning;
- Get Logs Keylogger – starting keystrokes intercepting;
- Show message box – showing dialog box with the text specified in the command;
- Show Push Notification – showing push notifications whose contents are specified in the command;
- Show Automatically push notification – showing push notifications whose contents are set in the Trojan's code;
- Start fake-locker – blocking the screen of the device window WebView, which showed the content received from the server web page;
- Get number from phone book – sending all the numbers from the contact list to the server;
- Sending SMS to your contacts – sending SMS messages to all numbers from the contact list;
- Request permission for injection – requesting permission to access data;
- Request permission for geolocation – requesting permission to access device location;
- Start Accessibility Service – requesting access to accessibility features (Accessibility Service);
- Start permission – requesting access to additional permissions;
- Start Forward Calls – launching calls redirection to the number specified by criminals;
- Stop Forward Calls – stopping calls redirection;
- Open Link in Browser – opening the specified link in a browser;
- Open Link in Activity – opening the link specified in command in WebView;
- CryptoLocker – encrypting files stored on the device and displaying a ransom request message;
- Decrypt File System – decrypting files;
- Record Sound – launching the recording of surroundings using the built-in microphone;
- Get IP Bot – determining an IP address;
- Kill Bot – cleaning up its configuration file and stopping the malicious application.
The Trojan has remote access to infected devices, which allows attackers to use it as a remote administration tool (RAT, Remote Administration Tool).Android.BankBot.325.origin is able to:
- retrieve the list of files, which are stored in the memory of the infected smartphones or tablets;
- upon a command from cybercriminals it loads any files to managing server as well as delete them;
- perform the audio recording using the built-in microphone;
- track all that happens on the screen, making screenshots and delivering them to server;
Android.BankBot.325.origin tracks the launch of a number of banking applications, applications for working with payment systems, social networks, cryptocurrencies, as well the launch of messengers and other popular software. Among these programs can be the following:
- com.whatsapp – WhatsApp Messenger;
- com.tencent.mm – WeChat;
- com.ubercab – Uber;
- com.viber.voip – Viber Messenger;
- com.snapchat.android – Snapchat;
- com.instagram.android – Instagram;
- com.imo.android.imoim – imo free video calls and chat;
- com.twitter.android – Twitter;
- com.facebook.katana – Facebook;
- com.facebook.orca – Messenger;
- com.google.android.gm – Gmail;
- com.google.android.apps.inbox – Inbox by Gmail;
- com.mail.mobile.android.mail – mail.com mail;
- com.connectivityapps.hotmail – Connect for Hotmail;
- com.paypal.android.p2pmobile – PayPal;
- com.amazon.mShop.android.shopping – Amazon Shopping;
- com.ebay.mobile – eBay - Buy, Sell & Save Money with Discount Deals;
- com.bmo.mobile – BMO Mobile Banking;
- com.cibc.android.mobi – CIBC Mobile Banking®;
- com.rbc.mobile.android – RBC Mobile;
- com.scotiabank.mobile – Scotiabank Mobile Banking;
- com.td – TD Canada;
- com.citibank.mobile.au – Citibank Australia;
- com.chase.sig.android – Chase Mobile;
- com.infonow.bofa – Bank of America Mobile Banking;
- com.konylabs.capitalone – Capital One® Mobile;
- com.clairmail.fth – Fifth Third Mobile Banking;
- com.moneybookers.skrillpayments – Skrill;
- com.moneybookers.skrillpayments.neteller – NETELLER;
- com.suntrust.mobilebanking – SunTrust Mobile App;
- com.usaa.mobile.android.usaa – USAA Mobile;
- com.usbank.mobilebanking – U.S. Bank;
- com.wf.wellsfargomobile – Wells Fargo Mobile;
- es.lacaixa.mobile.android.newwapicon – CaixaBank;
- es.evobanco.bancamovil – EVO Banco móvil;
- es.bancopopular.nbmpopular – Popular;
- com.tecnocom.cajalaboral – Banca Móvil Laboral Kutxa;
- com.rsi – ruralvía;
- com.kutxabank.android – Kutxabank;
- com.bankinter.launcher – Bankinter Móvil;
- com.bbva.netcash – BBVA net cash | España & Portugal;
- com.bbva.bbvacontigo – BBVA | España;
- es.bancosantander.apps – Santander;
- es.cm.android – Bankia;
- uk.co.bankofscotland.businessbank – Bank of Scotland Business Mobile Banking;
- com.rbs.mobile.android.natwestoffshore – NatWest Offshore;
- com.rbs.mobile.investisir – RBS Investor & Media Relations;
- uk.co.santander.santanderUK – Personal Banking;
- com.ifs.banking.fiid4202 – TSBBank Mobile Banking;
- com.rbs.mobile.android.ubr – Ulster Bank ROI;
- com.htsu.hsbcpersonalbanking – HSBC Mobile Banking;
- com.grppl.android.shell.halifax – Halifax: the banking app that gives you extra;
- com.grppl.android.shell.CMBlloydsTSB73 – Lloyds Bank Mobile Banking;
- com.barclays.android.barclaysmobilebanking – Barclays Mobile Banking;
- com.ing.mobile – ING Bankieren;
- com.unionbank.ecommerce.mobile.android – Union Bank Mobile Banking;
- com.snapwork.IDBI – IDBI Bank GO Mobile+;
- com.snapwork.hdfc – HDFC Bank MobileBanking;
- com.sbi.SBIFreedomPlus – SBI Anywhere Personal;
- hdfcbank.hdfcquickbank – HDFC Bank MobileBanking LITE;
- com.csam.icici.bank.imobile – iMobile by ICICI Bank;
- in.co.bankofbaroda.mpassbook – Baroda mPassbook;
- com.axis.mobile – Axis Mobile;
- com.infrasofttech.indianBank – IndPay;
- com.mobikwik_new – Recharge, Payments & Wallet;
- com.oxigen.oxigenwallet – Bill Payment & Recharge,Wallet;
- eu.inmite.prj.kb.mobilbank – Mobilní banka;
- cz.airbank.android – My Air;
- sk.sporoapps.accounts – Účty;
- cz.csob.smartbanking – ČSOB SmartBanking;
- cz.sberbankcz – Smart Banking;
- com.cleverlance.csas.servis24 – SERVIS 24 Mobilní banka;
- org.westpac.bank – Westpac Mobile Banking;
- nz.co.westpac – Westpac One Mobile Banking;
- au.com.suncorp.SuncorpBank – Suncorp Bank;
- org.stgeorge.bank – St.George Mobile Banking;
- org.banksa.bank – BankSA Mobile Banking;
- au.com.newcastlepermanent – NPBS Mobile Banking;
- au.com.nab.mobile – NAB Mobile Banking;
- au.com.mebank.banking – ME Bank;
- au.com.ingdirect.android – ING Australia Banking;
- com.imb.banking2 – IMB.Banking;
- com.fusion.ATMLocator – People's Choice Credit Union;
- au.com.cua.mb – CUA;
- com.commbank.netbank – CommBank;
- org.bom.bank – Bank of Melbourne Mobile Banking;
- com.bendigobank.mobile – Bendigo Bank;
- au.com.bankwest.mobile – Bankwest;
- com.bankofqueensland.boq – BOQ Mobile;
- com.anz.android.gomoney – ANZ Australia;
- com.bankaustria.android.olb – Bank Austria MobileBanking;
- at.spardat.netbanking – ErsteBank/Sparkasse netbanking;
- at.spardat.bcrmobile – Touch 24 Banking BCR;
- at.volksbank.volksbankmobile – Volksbank Banking;
- com.isis_papyrus.raiffeisen_pay_eyewdg – Raiffeisen ELBA;
- at.easybank.mbanking – easybank;
- at.bawag.mbanking – BAWAG P.S.K.;
- com.akbank.android.apps.akbank_direkt – Akbank Direkt;
- com.finansbank.mobile.cepsube – QNB Finansbank Cep Şubesi;
- com.garanti.cepsubesi – Garanti Mobile Banking;
- com.tmobtech.halkbank – Halkbank Mobil;
- com.softtech.isbankasi – İşTablet;
- com.ykb.android – Yapı Kredi Mobile;
- com.ziraat.ziraatmobil – Ziraat Mobil;
- com.pozitron.iscep – İşCep;
- com.vakifbank.mobile – VakıfBank Mobil Bankacılık;
- com.starfinanz.smob.android.sfinanzstatus – Sparkasse Ihre mobile Filiale;
- de.comdirect.android – comdirect mobile App;
- de.commerzbanking.mobil – Commerzbank Banking App;
- de.consorsbank – Consorsbank;
- com.db.mm.deutschebank – Meine Bank;
- de.dkb.portalapp – DKB-Banking;
- com.ing.diba.mbbr2 – ING-DiBa Banking + Brokerage;
- de.postbank.finanzassistent – Postbank Finanzassistent;
- mobile.santander.de – Santander MobileBanking;
- com.starfinanz.smob.android.sbanking – Sparkasse+ Finanzen im Griff;
- de.fiducia.smartphone.android.banking.vr – VR-Banking;
- com.palatine.android.mobilebanking.prod – ePalatine Particuliers;
- fr.laposte.lapostemobile – La Poste - Services Postaux;
- com.cm_prod.bad – Crédit Mutuel;
- fr.creditagricole.androidapp – Ma Banque;
- fr.axa.monaxa – Mon AXA;
- fr.banquepopulaire.cyberplus – Banque Populaire;
- net.bnpparibas.mescomptes – Mes Comptes BNP Paribas;
- com.boursorama.android.clients – Boursorama Banque;
- com.caisseepargne.android.mobilebanking – Banque;
- fr.lcl.android.customerarea – Mes Comptes – LCL pour mobile;
- mobi.societegenerale.mobile.lappli – L'Appli Société Générale;
- ua.privatbank.ap24 – Приват24;
- ru.sberbankmobile – Сбербанк Онлайн;
- com.idamob.tinkoff.android – Tinkoff;
- ru.vtb24.mobilebanking.android – ВТБ-Онлайн;
- ru.alfabank.mobile.android – Альфа-Банк (Alfa-Bank);
- ru.mw – QIWI Wallet;
- com.bochk.com – BOCHK;
- com.dbs.hk.dbsmbanking – DBS digibank Hong Kong;
- com.FubonMobileClient –富邦香港;
- com.MobileTreeApp –大新銀行;
- com.mtel.androidbea – BEA 東亞銀行;
- hk.com.hsbc.hsbchkmobilebanking – HSBC HK Mobile Banking;
- com.aff.otpdirekt – OTP SmartBank;
- com.ideomobile.hapoalim – בנק הפועלים - ניהול החשבון;
- jp.co.aeonbank.android.passbook – イオン銀行通帳アプリかんたんログイン&残高・明細の確認;
- jp.co.netbkd – 住信SBIネット銀行;
- jp.co.rakuten_bank.rakutenbank – 楽天銀行 -個人のお客様向けアプリ;
- jp.co.sevenbank.AppPassbook – App Bankbook;
- jp.co.smbc.direct – 三井住友銀行アプリ;
- jp.co.smbc.direct – 三井住友銀行アプリ;
- com.barclays.ke.mobile.android.ui – Barclays Kenya;
- nz.co.anz.android.mobilebanking – ANZ goMoney New Zealand;
- nz.co.asb.asbmobile – ASB Mobile Banking;
- nz.co.bnz.droidbanking – BNZ Mobile;
- nz.co.kiwibank.mobile – Kiwibank Mobile Banking;
- com.getingroup.mobilebanking – Getin Mobile;
- eu.eleader.mobilebanking.pekao.firm – PekaoBiznes24;
- eu.eleader.mobilebanking.pekao – Bank Pekao;
- eu.eleader.mobilebanking.raiffeisen – Mobilny Bank;
- pl.bzwbk.bzwbk24 – BZWBK24 mobile;
- pl.ipko.mobile – Token iPKO;
- pl.mbank – mBank PL;
- com.advantage.RaiffeisenBank – Raiffeisen Smart Mobile;
- hr.asseco.android.jimba.mUCI.ro – Mobile Banking;
- may.maybank.android – Maybank MY;
- ro.btrl.mobile – Banca Transilvania;
- piuk.blockchain.android – Blockchain Wallet. Bitcoin, Bitcoin Cash, Ethereum;
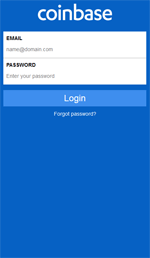
- com.coinbase.android – Bitcoin Wallet – Coinbase;
- com.unocoin.unocoinwallet – Unocoin Crypto Asset Exchange;
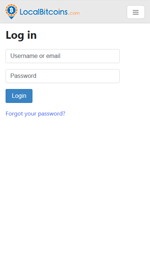
- com.localbitcoinsmbapp – LocalBitCoins Official;
- zebpay.Application – Zebpay Cryptocurrency Exchange.
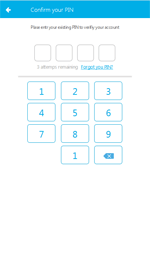
After launching one of the monitored applications, the Trojan displays a phishing login form of confidential information over its window, where it asks the user to enter a username, password and other sensitive data.
Examples of the phishing windows, displayed by banking Trojan: