A Trojan designed to gain authorized access to bank accounts of Android devices' users. The malicious program can be distributed in the guise of various applications. Once launched, it attempts to gain administrator privileges. After that, the Trojan removes its shortcut from the Home Screen.
 |
 |
Gathering information regarding the infected device
Using a POST HTTP request, the Trojan uploads the following information to the server at http://xxx.xxx.66.249/common/servlet/SendDevice:
- Phone number
- SIM card serial number
- Mobile device model
- OS version
- List of installed online banking applications from the targeted financial institutions
- Mobile network operator
Stealing data from contact list
Furthermore, information about the user's contacts is sent to the server at http://xxx.xxx.66.249/common/servlet/ContactsUpload. The data is transmitted in JSON format via a request that looks as follows: {"contacts":[{"mobile":"Example_number","name":"Example_contact"}],"mobile":"self_number"}, where “self_number” stands for the serial number of the infected device's SIM card.
Blocking incoming calls and SMS messages
Android.BankBot.20.origin can block all incoming calls and intercept SMS messages. It should be noted that calls and messages are blocked during a specific time period, starting on June 20, 2014, and ending on the date specified in the settings of the malware (depends on the version). All intercepted messages (new incoming and already stored on the device) are uploaded to the servers at
http://xxx.xxx.66.249/common/servlet/SendMassage,
http://xxx.xxx.66.249//common/servlet/SendMassage2.
Unauthorized sending of SMS messages
The Trojan can covertly send SMS messages. For that purpose, it sends the server at http://xxx.xxx.66.249/common/servlet/GetMessage a JSON request that looks as follows: {"id":"2","mobile":"self_number"}, where “self_number” stands for the serial number of the infected device's SIM card. The server replies with a JSON request ({"content":"sms_cont","tomobile"":"sms_numb"}) and sends a message with the text specified by “sms_cont” to the number specified by the “sms_numb” parameter.
Stealing bank account information
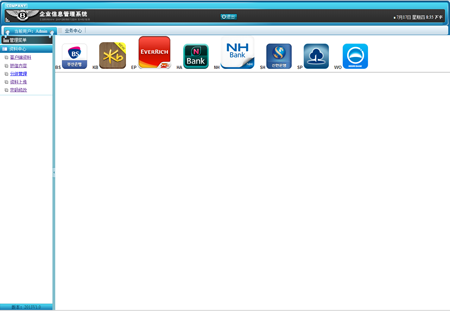
The main feature of Android.BankBot.20.origin is to replace legitimate online banking applications with fake ones. To do that, the Trojan runs a search for the following applications:
- nh.smart,
- com.shinhan.sbanking,
- com.webcash.wooribank,
- com.kbstar.kbbank,
- com.hanabank.ebk.channel.android.hananbank,
- com.epost.psf.sdsi,
- com.smg.spbs,
- com.areo.bs.
The compiled list is uploaded to the remote server at http://xxx.xxx.66.249/common/servlet/GetPkg, after which cybercriminals can command the Trojan to download a particular version of a fake banking application. This version is placed in the /sdcard/Download/update directory. After that, the malicious program initiates installation of the downloaded software by displaying the following update prompt: «새로운버전이 출시되었습니다. 재설치 후 이용하시기 바랍니다». The legitimate programs replaced by the fake ones are removed. The installed copies of legitimate applications imitate their interface and urge users to enter their authorization data, so that cybercriminals can gain access to bank accounts of their victims.
C&C server
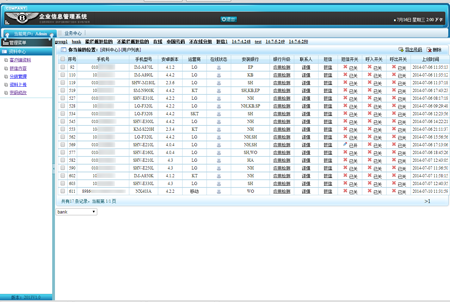
Using the administrator panel of the command and control server, cybercriminals can monitor infection statistics and control bots.
Summery statistics on infected devices
Fake banking applications' installation
By default, the Trojan communicates with a command and control server at http://xxx.xxx.66.249/. However, cybercriminals can change the address by sending an SMS message that looks as follows: “V:www.commandcenterurl.com”.