This is a Trojan for Android that is attacking South Korean users. It is intended to remove a number of banking applications and replace them with fake versions as well as execute malicious commands issued by cybercriminals. This Trojan is an executable dex file for Android (Dalvik executable). It is launched by Android.MulDrop.46.origin, which can be distributed by attackers in the guise of legitimate software.
Communication with the command and control server and execution of cybercriminals' commands
To determine the IP address of the command and control server, Android.BankBot.35.origin connects to the following remote hosts:
http://[xxx].[xxx].85.17:5245/dns.asp?name=sdk[xxx].vi[xx].co
http://m.[xxx]ne.com/profile?hostuin=[xxxxxx]1716
http://[xxx].[xxx].85.17:5245/dns.asp?name=xiao[xx].ie[xx].net.
Once connected to the command and control center, Android.BankBot.35.origin sends there the following information in JSON format:
- the type of the mobile network;
- the type of active Internet connection (mobile Internet or Wi-Fi);
- the Wi-Fi signal level;
- the information about a SIM card presence;
- the user's phone number;
- the battery charge level;
- the IMEI;
- the Trojan version;
- the unique Trojan's ID;
- the information requested on the command.
In return, the malware gets the list of controlling commands (also in JSON format). Once received instructions from cybercriminals, Android.BankBot.35.origin is able to perform the following:
- Send SMS with a specific text to a specified number.
- Enable or disable Wi-Fi.
- Upload data from the phone book (including the phone numbers saved in the SIM card) to the server.
- Download a specified dex file from the remote host and run it.
Replacement of legitimate banking applications
Every 90 seconds, the Trojan checks the availability of one of the following bank's applications on the mobile device:
- com.wooribank.pib.smart;
- com.kbstar.kbbank;
- com.ibk.neobanking;
- com.sc.danb.scbankapp;
- com.shinhan.sbanking;
- com.hanabank.ebk.channel.android.hananbank;
- nh.smart;
- com.epost.psf.sdsi;
- com.kftc.kjbsmb;
- com.smg.spbs.
If one of them is found, Android.BankBot.35.origin connects to a command and control server and downloads the appropriate fake version:
http://[xxx].[xxx].245.166:6545/ *pk_name*.apk is the name of the malicious fake banking program. Thus, the Trojan may download the following applications (detected as Android.MulDrop.46.origin):
- com.cash.apc.woori.kr.android.apd;
- com.kr.androids.kbstar.kbbankings.app;
- com.ibk.korea.kr.androids.ibkbanking;
- com.goog.sc.android.dadbdkr.scbankapp;
- com.android.google.shinhanbbk.kr.app;
- com.hana.google.kr.channel.korea.app;
- com.we.google.nhb.kr.bk.app;
- com.android.post.fsps.kr.wu.sdsi;
- com.kr.android.ftkc.kjb.kjbsmb.app;
- com.androids.kr.kf.androids.sm.spb
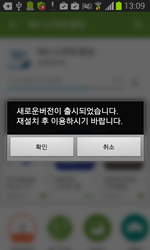
Once downloaded the necessary software, Android.BankBot.35.origin prompts the user to install a supposedly new version of the banking program:
With the user's consent the Trojan removes the legitimate program and installs the bogus one.
Publishing additional components
Additional dex files, downloaded by the Trojan, are run by Android.MulDrop.46.origin. To do this, the similar method, that is applied to launch Android.BankBot.35.origin, is used (applying the DexClassLoader class, so the user is not involved in this process).
Blocking of SMS messages
Android.BankBot.35.origin is able to block and intercept SMS messages from certain phone numbers. Information on these numbers is in the Trojan's black list.
Self-Protection Mechanism
Android.BankBot.35.origin incorporates the feature of self-protection. Every 2 seconds (for Android.BankBot.36.origin—every 0.2 seconds) the malware checks whether the following applications are active:
- com.estsoft.alyac.ui (popular South Korean anti-virus);
- packageinstaller.UninstallerActivity (System applications management tool);
- *.DeviceAdminAdd (interface for managing the mobile device administrators).
If at least one of them starts, Android.BankBot.35.origin returns the user to the home screen:
if(v3 != 0 || v4 != 0 || v5 != 0) {
Intent v2 = new Intent("android.intent.action.MAIN");
v2.addCategory("android.intent.category.HOME");
v2.addFlags(268435456);
this.this$1.this$0.service.startActivity(v2);This self-defense is not active if the user does not provide the Trojan with mobile device's administrator privileges, or if at least one legitimate banking application, that Android.BankBot.35.origin did not manage to fake, is still installed.